Browser extensions downloaded almost 33 million times from Google’s Chrome Web Store covertly downloaded highly sensitive user information, a security firm said on Thursday in a report that underscores lax security measures that continue to put Internet users at risk.
The extensions, which Google removed only after being privately notified of them, actively siphoned data such as screenshots, contents in device clipboards, browser cookies used to log in to websites, and keystrokes such as passwords, researchers from security firm Awake told me. Many of the extensions were modular, meaning once installed, they updated themselves with executable files, which in many cases were specific to the operating system they ran on. Awake provided additional details in this report.
Company researchers found that all 111 of the extensions it identified as malicious connected to Internet domains registered through Israel-based GalComm. The researchers eventually found more than 15,000 registered through GalComm hosting malicious or suspicious behavior. The malicious domains used a variety of evasion techniques to avoid being labeled as malicious by security products.
Awake analyzed more than 100 networks across financial services, oil and gas, media and entertainment, health care and pharmaceuticals, retail, and three other industries. Awake found that the actors behind the activities had established a persistent foothold in almost all of those fields. The attackers’ use of Google and a domain register accredited by the Internet Corporation for Assigned Names and Numbers—and the ability to evade detection by security firms—underscores the frequent failure of tech companies in safeguarding Internet security.
“Trust in the Internet and its infrastructure is critical,” Awake wrote in a summary of its findings. “Exploiting key components of this infrastructure—domain registration, browsers, etc.—shakes the foundation of trust and represents a risk to organizations and consumers alike. The research shows three critical areas of fragility with the Internet that are being exploited to passively, but maliciously surveil users.”
Feels like the first time… NOT!
Awake’s findings are hardly the first report of browser extensions hosted on Google servers being used maliciously against Chrome users. In an exclusive article posted last July, Ars reported on extensions—mostly hosted by Google—that collected 4.1 million users’ browsing histories and openly published them on a fee-based analytics site. The data included proprietary data from Tesla, Jeff Bezos’ Blue Origin, and dozens of other companies. Over the years, there have been dozens of other discoveries of malicious Chrome extensions, with one of the more recent ones occurring in February.
In a statement, Google officials on Thursday wrote:
We appreciate the work of the research community, and when we are alerted of extensions in the Web Store that violate our policies, we take action and use those incidents as training material to improve our automated and manual analyses. We do regular sweeps to find extensions using similar techniques, code, and behaviors, and take down those extensions if they violate our policies.
All extensions go through an automated review process, and the majority also undergo manual reviews by our team. We use a combination of automated and manual review, based on a variety of signals for a particular extension. You can view our full program policies here.
The Chrome Web Store uses a number of methods to detect policy violations and enforce against them, including manual and automated reviews both proactively and responsively. Enforcement action can include removal from the Chrome Web Store or developer account termination. In addition to disabling the accounts of developers that violate our policies, we also flag certain malicious patterns we detect in order to prevent extensions from returning. Additionally, we’ve announced technical changes that will further strengthen the privacy of Chrome extensions and new policies that improve user privacy.
Officials from GalComm did not respond to an email seeking comment for this post.
The extensions posed as document readers, such as those below:
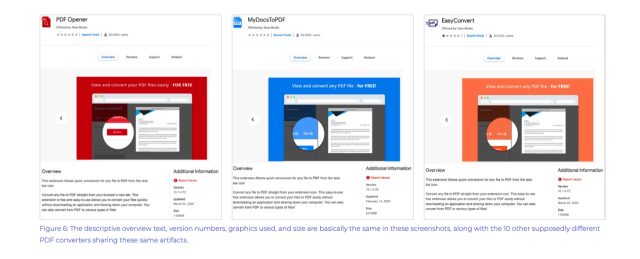
Awake
Others pretended to provide security enhancements:
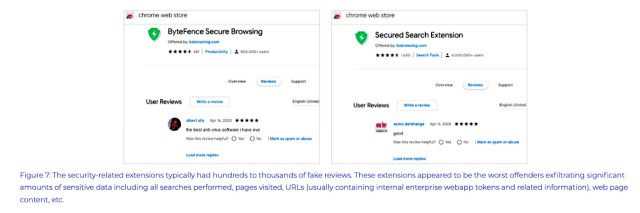
Awake
Few of them provided the capabilities they claimed. A full list of the extensions Awake found can be found in this Excel spreadsheet. (Those who don’t trust opening an Excel spreadsheet can upload it to Google Docs and read it there. An alternative is to read a list in the above-linked report, but it lists only the extension ID and not the name.)
While the 33 million installations may be inflated with artificial downloads, Awake said it believes the number of devices infected in this campaign is likely close to that number. Because the number is based on extensions that were in the Chrome Web Store at the beginning of May, it likely leaves out extensions that were available earlier and later removed. The number also doesn’t count extensions that were available from channels outside of the Chrome Web Store.
The malicious domains that Awake identified are here.
While Google scans extensions before posting them to the Chrome Web Store and removes extensions when it learns its process has failed, the process regularly fails, often to the detriment of millions of users. The company usually provides scant notice to Chrome users whose privacy or security has been compromised.
The upshot is that users of any browser should install extensions sparingly and only when they provide real value. When you do install one, try to choose one from a known developer or at least one with a website or social media handle that you can research. Don’t forget to read comments for reports of suspicious behavior.
People should also periodically check their extensions page to check for notifications that have been removed or found to violate the browser maker’s terms of service. While there, remove any extensions that haven’t been used in a while or are no longer needed.
