It’s human nature to get scared in October. Chill winds and lengthening shadows in the Northern Hemisphere foretell lean times and long, dark nights. If Halloween (or All Saints’ Day) wasn’t during this time of year, it would eventually migrate to it. And it isn’t just children who get scared — financiers do, too; more stock market crashes happen in October than random chance would suggest.
So it’s apropos that October is also National Cybersecurity Awareness Month (NCSAM). Sure, it’s also National Sausage Month (not scary), Raptor Month (somewhat scary), and American Cheese Month (moderate-to-severely scary), but those awareness campaigns honestly pale in comparison to the NCSAM, which is now in its 16th year!
While the young people revel in their fright with scary Momo challenge costumes and parties, the security and risk professionals need no additional accoutrements to fuel their anxiety. Consider the trends in 2019:
- Ransomware attacks against enterprises are up 500% from last year, according to “Forrester’s Guide To Paying Ransomware.” Threat actors are becoming increasingly sophisticated in how they ply their trade: identifying the critical assets to interfere with core business functions, seeking out and specifically targeting your backup systems to undermine your ability to recover, and, in some cases, researching your company’s financial situation to know exactly how the attack is affecting it and how much you can afford to pay. Ransomware is a business, and these actors want to get paid.
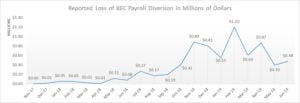
- BEC losses reach $29 billion. While everyone is out there trying to secure Kubernetes pods and outsmart quantum computers, attackers have been quietly racking up enormous wins with the simplest threat vector of all: plain-text business email compromise (BEC). On September 10, the FBI released data collected over three years showing the dollar exposure against BEC. Payroll employees have been favorite targets, and payroll diversion schemes in the past 18 months have led to a loss of $8.3B.
- Data breaches have become the norm. According to a recent Forrester report (“Security Outlook 2019: Modest Growth, But Some Sectors Will See Double-Digit Increases“), 50% of global network security decision makers reported that their firm experienced a breach of sensitive data in the past 12 months, up from 43% in 2015. More concerningly, 25% reported experiencing at least three breaches; 9% said they experienced six or more breaches. You don’t even want to know how many the top 1% experienced.
But this October shouldn’t be all about doom and gloom. There have been some excellent industry publications around Zero Trust, processes, and policy architecture published just this month or last. So instead of increasing our self-medication regimens, security and risk professionals can arm our teams better with these five following pieces:
- Forrester report: “Gauge Your ZTX Security Maturity” (October 11). To convert your digital business ecosystem into a secure, Zero Trust eXtended (ZTX) ecosystem, you need to know where to start the transformation. This report guides security and risk pros through Forrester’s ZTX maturity assessment so you can gauge where your firm is on its journey and discover which core competencies you need to strengthen or develop.
- OWASP list: OWASP API Security Top 10 (September 30). By nature, APIs expose application logic and sensitive data such as personally identifiable information (PII) and, because of this, have increasingly become a target for attackers. API security focuses on strategies and solutions to understand and mitigate the unique vuln
- Forrester report: “The Eight Business And Security Benefits Of Zero Trust” (September 25). Devoting resources to the granular aspects of networks is understandable and necessary to a degree, but it’s also a great way to lose sight of your ultimate goal: protecting customers and empowering the business. Zero Trust networks accomplish the dual tasks of deep, continuous data inspection across the network and lean operation and oversight — tasks that seem mutually exclusive in traditional networks. This report highlights the eight most significant ways Zero Trust boosts security and your business.
- NIST SP 800-207: Zero Trust Architecture (September). The National Institute of Standards and Technology (NIST) has released a draft of its Zero Trust architecture (ZTA), available for comment now. This publication discusses the core logical components that make up NIST’s interpretation of Zero Trust architecture network strategy. Its focus on protecting resources rather than network segments is a response to enterprise trends that include remote users and cloud-based assets that are not located within an enterprise-owned network boundary. The document defines an abstraction of ZTA and discusses use cases where ZTA could improve an enterprise’s overall IT security posture.
- Forrester report: “Now Tech: Security Awareness And Training Solutions, Q1 2019” (January 23). You can use security awareness and training solutions to build the ever-important human firewall, prepare your workforce for recognizing and responding to phishing and BEC attacks, and rebrand security as a business enabler. But to access these benefits, you’ll first have to select from a diverse set of vendors — vendors that vary by size, functionality, geography, and vertical market focus. Use this Now Tech report to understand the value you can expect from a user awareness and training provider and select vendors based on size and functionality.
Most of these resources were published either during National Cybersecurity Month or within spitting distance of it. The NIST framework is under review, and comments are being accepted through October and into November. Let this library of defensive collateral provide some comfort to security and risk professionals all around the world as we head into the dark days of winter.
And one more thing: For many organizations, October is also budgeting month for the following fiscal year. Don’t forget to include budget room for cybersecurity awareness training, cyberinsurance, OWASP dues, Zero Trust Certification training, and, of course, the renewal of your Forrester client membership.