
Hackers are actively unleashing attacks that attempt to steal encryption keys, passwords, and other sensitive data from servers that have failed to apply critical fixes for two widely used virtual private network (VPN) products, researchers said.
The vulnerabilities can be exploited by sending unpatched servers Web requests that contain a special sequence of characters, researchers at the Black Hat security conference in Las Vegas said earlier this month. The pre-authorization file-reading vulnerabilities resided in the Fortigate SSL VPN, installed on about 480,000 servers, and the competing Pulse Secure SSL VPN, installed on about 50,000 machines, researchers from Devcore Security Consulting reported.
The Devcore researchers discovered other critical vulnerabilities in both products. These make it possible for attackers to, among other things, remotely execute malicious code and change passwords. Patches for the Fortigate VPN became available in May and in April for Pulse Secure. But installing the patches can often cause service disruptions that prevent businesses from carrying out essential tasks.
Internet scans performed on Saturday by security intelligence service Bad Packets show there are 2,658 Pulse Secure VPN endpoints vulnerable to flaw currently being exploited. The scans found that vulnerable endpoints belonged to a variety of sensitive organizations, including:
- US military, federal, state, and local governments agencies
- Public universities and schools
- Hospitals and health care providers
- Major financial institutions
- Other Fortune 500 companies
Below is a breakdown of where the endpoints are located:
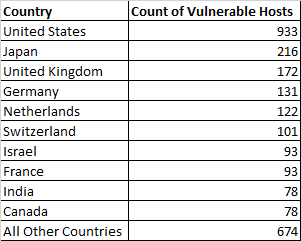
BadPackets
Spraying the Internet
Over the past 36 hours, hackers have started spraying the Internet with code that attempts to opportunistically exploit that difficulty, independent researcher Kevin Beaumont said. He said he found attacks against Fortigate servers coming from 91.121.209.213, an IP address that has a history of previous misconduct. A scan on Friday using the BinaryEdge search engine showed a new IP address, 52.56.148.178, had also begun spraying exploits for the same vulnerability.
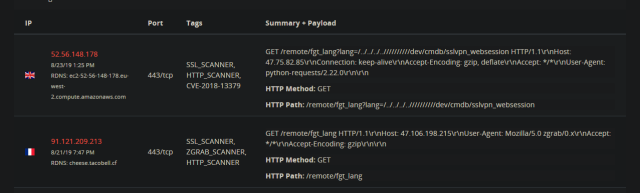
Earlier this month, two samples of exploit code for CVE-2018-13379, as the vulnerability is tracked, became publicly available here and here. The first one actually obtains data stored on vulnerable machines, while the latter merely checks if a machine is vulnerable.
Meanwhile, Beaumont said, attacks trying to exploit unpatched Pulse Secure servers are coming from 2.137.127.2. Exploit code became publicly available earlier this week. Troy Mursch, the independent researcher behind Bad Packets, said he also found attacks coming from 81.40.150.167 that also attempt to exploit or test for the vulnerability, which is indexed as CVE-2019-11510. In the event one of the mass scans identifies a vulnerable server, it may then exploit a code-execution flaw the Devcore researchers also discovered.
“These scans are targeting endpoints that are vulnerable to arbitrary file reading leading to sensitive information disclosure of private keys and user passwords,” Mursch told Ars. “These credentials can then be used to conduct further command injection attacks (CVE-2019-11539) and gain access to the private network allowing for further malicious activity.”
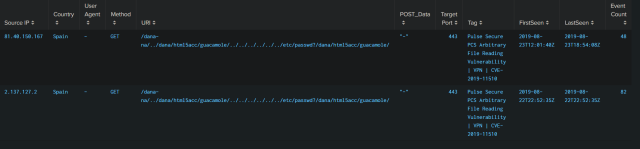
Mursch said the honeypot server he used to detect the attacks was also able to identify that the IP address 2.137.127.2 was also targeting the Pulse Secure vulnerability. He said he didn’t believe either of the IPs was operated by a researcher who was merely scanning for unpatched servers. His honeypot was unable to detect code attacking the Fortigate vulnerability. Beaumont was using a honeypot provided by BinaryEdge.
The vulnerabilities are serious because they affect a piece of software that’s required to be accessible to the Internet and that acts as a gateway to highly sensitive parts of an organization’s network. Obtaining hashed and in some cases plain-text passwords, encryption keys, and other sensitive data, could allow people to penetrate those networks. With more work, attackers who identify unpatched servers could also exploit the other vulnerabilities the Devcore researchers found. One Fortigate flaw, which they dubbed “The Magic Backdoor,” allows remote attackers who know a hard-coded key to change passwords.
Representatives from both Fortinet and Pulse Secure said the companies have been urging customers for months to patch their systems as soon as possible. Neither company could confirm or expand upon the reports of scanning coming from Beaumont and Mursch. Organizations using either of these VPNs should take time now to make sure they’re not vulnerable.