Advertisers selling a product or service on the web try to predict every possible scenario so that is can be manipulated to increase odds that you will buy.
From awareness about the offer through ads to actual purchase, or “conversion,” every step of the buying cycle is meticulously analyzed to achieve better results changing “visitors” into “customers.”
Sophisticated ad campaign tracking amplified by targeting technologies and algorithm-based behavioral data analysis provide a steady influx of interested visitors, but that’s merely step one for an advertiser. The outcome of the customer’s journey to purchase depends on a website’s usability, sufficiency of information about the product and seller, price and extra services, as well as security and payment methods available.
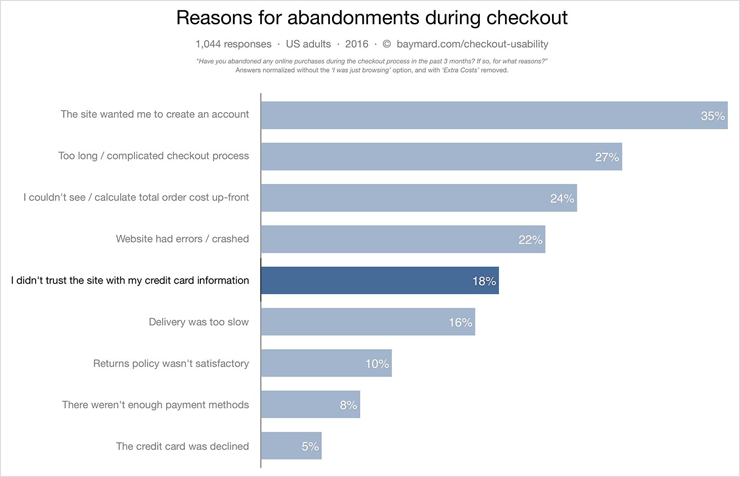
A combination of these factors translates into an emotion of trust which is decisive in our journey as customers. However, sometimes it’s not enough. One of the main concerns of e-shoppers is the security of the financial transactions and card details on sites. According to a study by Baymard Institute “How users perceive security during checkout,” 18 percent of users didn’t trust the website with their credit card info, abandoning the shopping cart. To convince users to trust a brand or site, advertisers have been using trust seals and logos on key pages, like the shopping cart, checkout page or registration page.
Significant percentage of users is reluctant to trust websites, when it comes to their financial info
In this article, we will discuss what exactly do some of the most well known site trust seals and logos mean to you as a customer and what is their proper usage. Sadly, fake seals/logos are widely used by cyber crooks out there, so we’ll discuss verification, which should help you to tell a real logo from a fake one.
From Perceived Safety to Understanding the Meaning of Trust Seals
During Baymard Institute’s “Checkout Usability Test,” researchers observed that many users “perceive” certain parts of checkout page as more “trustworthy” than the others. Parts of the page that contained trust or security seals have been perceived as safer ones.
Checkout page example #1
Checkout example #2
Out of these two examples many users would prefer the second one. It is perceived as more “robust” because of design and trust logos, giving a sense of improved safety when submitting card details. It is worth noting that each of the three logos in the second example verify a different aspect of safety, but most of non-technical customers would describe it as “trusted” or “safe”.
Trust is largely based on “feeling” rather than understanding technological details and advantages. In the case of example two, this feeling is assured by adding a “Secured” trust seal image issued by SSL/TLS certificate authority GeoTrust.
In reality, both websites above are using HTTPS/TLS connection protocol, which means that data including personal info and payment credentials is encrypted when communication between the browser and the website occurs. Additionally, a website’s SSL/TLS certificate verifies its authenticity. Customer’s browser shows the secure connection state in the address bar:
Checkout example #1
Checkout example #2
The underlying problem here is that without understanding the functions and differences between the trust seals, customers may fall for fraudulent offers, lose their sensitive data, or run into bad customer service. After all, a green browser bar indication and optional trust seal on the pages can tell you whether the connection is secure, but they can’t tell anything about the quality of the product or ethical business practices of a certain e-commerce website.
There are several types of trust seals that are granted to websites by issuing organizations after said websites undergo a vetting process according to the issuer’s requirements. The most common types are:
- Website security seals (SSL/TLS certificates + trust seals indicating their usage)
- Privacy-related seals (Certifying that website’s practices are in-line with privacy regulations and customers may trust the website’s Privacy Policy)
Let’s take a closer look at these two groups one-by-one.
Website Security Seals
Site security seals are issued with a SSL/TLS website certificate and may be placed on a website pages. Generally some of the biggest certificate authorities (issuers) are antivirus companies and privacy-related entities, like Symantec, TrustArc, Comodo and McAffee.
There are two types of SSL/TLS certificates, that users should know of: Standard SSL and Extended Validation SSL/TLS. Both of those allow a website owner to use the website security seal provided by the certificate authority. However, vetting of the website applying for certificate and trust seal differs. In the case of Standard SSL/TLS, certificate authority representatives will thoroughly review a website’s application and verify businesses information to make sure it’s a legitimate entity applying for the certificate.
For and Extended Validation SSL/TLS Certificate, the website and organization vetting process is extremely strict and involves a number of extra checks by an certificate authority.
Websites using Extended Validation SSL/TLS certificates are the safest to use. Here’s an easy way to tell the difference between the two:
SSL and Extended Validation SSL certificate marking in the browser bar
Recommended for You
Webcast, November 2nd: How to Get Your Lost Rankings Back in Google (Quickly!)
Here’s an example of Standard Validation SSL certificate usage with a Norton Secured Trust seal:
Norton Secure Seal and the information on its website report
When clicking on a seal, users may verify that the website is using a certificate issued by trusted authority and the website and business have indeed been verified. Users also have an option to report the certificate misuse if they notice something suspicious.
If the website bar doesn’t indicate the usage of any of these two types of certificates, yet it contains trust seals, double check them using this tool from Comodo. In case the certificate has been revoked, avoid sharing sensitive data with the website and report to an issuer of website security seal. Websites with security seal are also scanned for malware and vulnerabilities on a daily basis during the period of certificate validity.
Privacy-related Trust Seals
There are several well known companies, one of them is TrustArc, formerly known as TRUSTe. They position themselves as a consulting/technology platform providing compliance/consulting services for businesses looking to win the trust of their customers. Despite the trouble TrustArc got into for failing to certify websites and of some of their clients in time, it still operates and their trust seal below is recognized by significant part of US audience.
TRUSTe is now known as TrustArc
Other types of trust seals issued by entities like the Better Business Bureau or Trust Pilot are granted to businesses for meeting business standards promoted by these entities. It is worth noting that in many cases with such entities the eligibility of certain company for becoming “qualified” depends on the willingness to pay membership fee.
What Do US Consumers Think of Trust Seals
According a 2013 Baymard Institute study, Norton was leading as the most trusted (or simply most recognized?) seal.
Baymard institute study on the most trusted website seals,2013
Newer findings by Conversionxl (2017) suggest that brand familiarity of an entity issuing certain trust seal translates into trust when paying online.
Conversionxl study from 2017 shows affinity between issuing entity’s brand familiarity and trust to the website where the seal is placed
Trust Seal or Trust Trap?
Based on the previously mentioned studies, it is clear that simply seeing a trust seal from a well known company may be a sufficient reason to make a purchase, and it’s already a habit for many. Nothing changed over time between these two studies. But, maybe not noticing trust logos plays a part. According to a >paper by researchers from University College of London, 38 percent of users in their study didn’t notice trust seals based on eye-tracking data.
Let’s look at Norton, which is still among the most trusted certificate authorities four years after Baymard Institute’s research. Norton’s trust seal is placed on literally millions of pages. Yet, nothing has been done to increase awareness about how to use it properly among the customers. Most of them aren’t even aware it’s clickable and contains data about the website’s security and SSL/TLS certificate. Website owners are aware that placing an image will bump up the percentage of buying customers and are pretty happy to pay for the next year of using the certificate and seal. Norton isn’t the only one of course, just look at the other names on the picture above.
Users should be asking themselves whether they are going trust these images blindly or should they treat them with some reasonable doubt. Here are few things to ponder:
- Some of the trust seals can be outright purchased, without stringent evaluation of the business (Think: Better Business Bureau.)
- Trust seals are granted to websitesbusinesses for a certain period, sometimes revalidation is delayed or postponed (Check the FTC report on TrustArc’s case above.)
- Some businesses selling shady or potentially unwanted software will still qualify to receive SSL/TLS certificate for their website and checkout pages, because well, they are a registered company with an office, etc. Certificate authorities don’t evaluate the product itself.
- From time to time even notorious certificate authorities fail to deliver their services as promised. Like in case with Norton, when their security seal service fails to perform security check of some websites.
- Not all trust seals can be verified by simply clicking the logo and checking its validity on the issuing entity’s website. Searching through the website may take up some time.
- Cyber crooks may easily copy any trust seal image and put it on a fake site to make their phishing or exploit dropper page look legit.
Trust Seals Misuse: Cases and Consequences
Adversaries trying to impersonate legitimate websites or businesses absolutely love trust seals. They are easy to copy. Moreover, you can’t really trace a copied image—not that certificate authorities care to track them anyway.
Here’s a classic example of logo misuse by an potentially unwanted software vendor.
An example of Norton Secured and Microsoft Partner logos misuse
The Norton Secured Seal is clearly misused since it’s given by Norton only to websites, purchasing SSL/TLS certificates from them. The same goes for the Microsoft Partner Network logo—it is prohibited to use in the partnering company’s product and its promotion.
Another variation of logo misuse I just grabbed off the Internet is used by tech support scams. Clearly they’re using some scareware methods: while a page is loading, browser navigation is blocked and several intrusive pop-ups appear, basically forcing the panicking user to dial a 1-800 phone number. Cyber criminals have learned that putting merely an image with Microsoft logo is enough to induce fear and make user call their fake “support line”.
Microsoft logo misuse by tech support scam
By now you probably feel like literally no one on the web can be trusted. But don’t overreact.
In fact , the intention of this article is to provide an understanding that no entity should be blindly trusted and there’s no silver bullet when it comes to safety on the web. These takeaways will help you to be more confident and prepared.
- Check the links you’re about to click, if they look suspicious, using Virustotal scanner, Norton Safeweb, Google SafeBrowsing Transparency Report
- Check whether you’re connecting to the site via HTTPS, and don’t forget to check the certificate, whether its SSL/TLS or Extended Validation SSL/TLS.
- Consider using the HTTPS Everywhere add-on, it’s available in Chrome and FireFox stores
- Take a look at what others have to say about a website, see if it has reviews. See if the contact info is listed. Bad English along with poor design and lack of content should alert you.
- Research the trust seals the site has, but don’t make a decision to share your data based on that.
- Make sure your antivirus is always on and updated