The keys to a successful second line of defence
There are many risk management methodologies in existence but it is not uncommon to come across large firms still following today simplistic, dysfunctional or flawed practices, in particular around operational risk management.
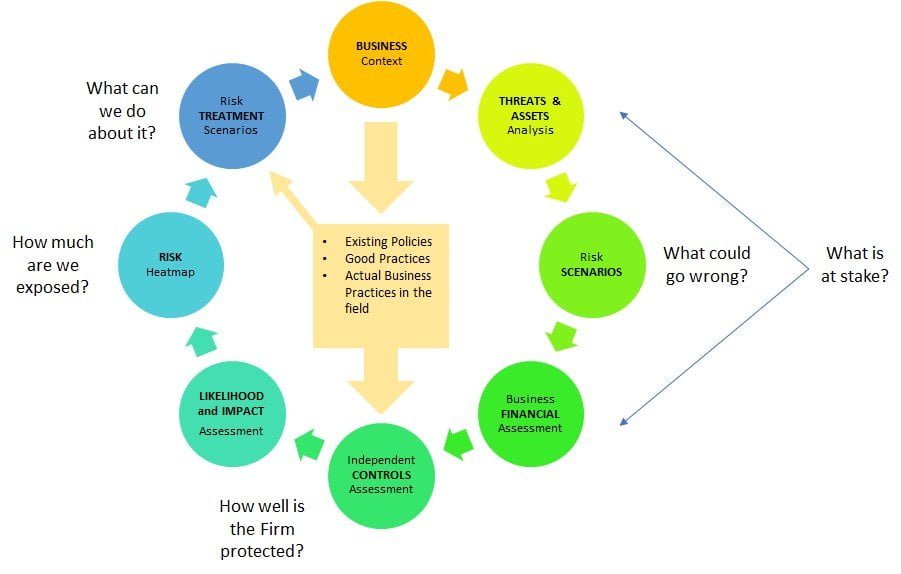
The main issue with many of those approaches is that they are plagued by a fundamental theoretical issue, which goes far beyond semantics: There is an abyss between managing “Risk” (broadly defined as “the impact of uncertainty on objectives”) and managing “risks” (events or scenarios that might have an undesirable outcome).
But many practitioners, when faced with the challenges of establishing a second line of defence type-of-function, still follow the path of least resistance and start with the arbitrary definition upfront of a series of “risks”, that are generally collected through workshops with senior executives in the business. In practice, that’s where many aspects start to go wrong, driven by a short-termist business agenda or a complacent “tick-in-the-box” management culture around compliance.
The dynamics of those workshops often revolve around “what keeps you awake at night” type of discussions, which force the participants to imagine situations where something could go seriously wrong and hit the firm. Participants generally engage with the process based on their own experience and ability to project themselves. Almost always, they draw on past experiences, things they have seen at other companies (in other jobs) or things they have heard of. Rarely are those stories based on hard facts directly pertinent to the firm and its problems. It often results in organic and very rich exchanges but also leads to an avalanche of scenarios, unstructured and often overlapping. The lack of rigour in the approach also results in most cases in a considerable language mix-up, with the description of the so-called “risks” combining shamelessly threats, controls and other elements – internal or external.
Then follows a second phase during which participants are asked to estimate how likely are those scenarios to affect the firm and what could be the resulting financial loss.
The first part (“how likely are those scenarios to affect the firm”) is plagued by a fundamental confusion between frequency and probability (in many cases, this is entirely by design i.e. participants being asked “could this happen weekly, monthly, annually?”). Again, participants tend to engage with the question by drawing on past experiences (the “bias of imaginability” theorised by Kahneman) or things they have seen elsewhere, irrespective of the actual context of the firm itself. At best, it results in “educated guesses”; at worst, we end up in pure “finger-in-the-air” territory.
The assessment of the potential financial losses is often more reliable, as this is an area where most of the senior executives involved would have more experience, and as long as the monetary brackets are wide enough, they are likely to put the various scenarios in the right buckets.
At the back of that, a risk “heat map” is drawn, a number of action plans are defined and a budgetary figure is put on each (in terms of the investment required to have an impact of the risk map). This is the point where risk is either “accepted”, “mitigated” or in theory “transferred”.
In practice, the impact of the proposed scenarios on the risk map is often estimated and rarely quantifiable, and the whole process is simply used to drive or justify a positive or negative investment decision, or to present an illusion of science to auditors or regulators.
The agreed actions are then given to a project manager or to a programme office to supervise, often with some form of progress reporting put in place back to a risk committee, with all sorts of convoluted KPIs and KRIs wrapped around it.
This whole approach is certainly better than doing nothing, but it is flawed at a number of levels. Essentially, it is vulnerable to political window-dressing from start to end, and the various estimations made by senior executives along the chain (willingly or unwillingly) can be used to adjust to any internal political agenda (e.g. presenting a particular picture to regulators, limiting expenditure, not having to confront boards or business units with an inconvenient truth).
Fundamentally, the “risks” being (allegedly) “managed” may have nothing to do with the actual reality of the firm, and even the “management” aspects may be disputable, in particular if the governance around the actual delivery of the agreed action plan is weak or inefficient (or, at the other end of the scale, bureaucratic and overly complex). This is more about “doing stuff” (at best) than “managing Risk” because of the colossal amount of assumptions made along the way.
Recommended for You
Webcast, December 14th: How to Create a Snapchat Strategy to Grow Your Business
There are 3 aspects that need to be addressed for those methods to work better and deliver proper results in terms of real “Risk Management”:
1- Talking to senior executives and running workshops with them is a good start, but they should be focused on “threats” – and not “risks” – and on the “assets” the “threats” may target. Focusing on threats and assets brings advantages at 2 levels: First it roots the language of the discussion in the reality of what is at stake, instead of hypothetical scenarios. Second, by following simple threat modelling practices, it offers a structure to guide the discussion with some rigour:
- Who are the people or organisations who could cause you harm? (the threat agents)
- What are their motivations? Their level of sophistication? The attack vectors they use? The attack surfaces they look for?
- What could they do to you?
By combining and ranking those factors, you arrive to a number of key scenarios that are rooted in the reality of the firm and its context, and in the process, you have forced the executives involved to face the reality of the firm, the world it operates in, and its real viciousness.
But for the result to be truly representative and meaningful, it is also essential to ensure that all stakeholders are involved across all geographies and corporate silos (business units, IT, Legal, HR, procurement, etc…), and to include key external business partners where business processes or IT facilities have been outsourced.
2- Asking executive management to place the resulting scenarios is broad financial loss buckets is a good step that is likely to work well as we indicated before, and could be kept, but the assessment of any form of probability of occurrence or potential impact should be dissociated from the discussion with executives at this stage and, again, firmly rooted in the reality of the firm through an independent assessment of the actual presence or absence of the necessary protective measures.
This is essential in focusing management on the fact that “managing Risk” is about protecting the firm from undesirable outcomes, and that it is achieved through the actual implementation of tangible measures that are known to protect, and can be:
- determined upfront based on the identified threat scenarios,
- mandated by policy or adherence to good practice,
- enforced through good governance, internally and with third-parties.
Risk is a by-product of the presence or absence of such measures, and the actual Risk “heat map” for the firm can be drawn in a quantified manner from those independent assessments, instead of being estimated.
3- Once the Risk “heat map” is firmly linked to the presence or absence of actual protective measures, it is possible to define risk treatment scenarios also linked to those measures and map in a quantified manner the impact they would have on the Risk “heat map”.
It is then possible to compare those Risk treatment scenarios and determine the most attractive for the firm. It also becomes possible to track and visualise progress in a quantifiable manner.
It is easy to argue that the governance issues around the actual delivery of agreed Risk treatment actions still remain (in particular for larger firms), and that the two approaches are fundamentally the same (one qualitative, and the other quantitative), but the quantitative approach is truer to its purpose (“managing Risk”), considerably richer in terms of managerial levers, and far less vulnerable to manipulation and window-dressing.