Microsoft’s Edge announced on Twitter Friday that an implementation of Safari’s Intelligent Tracking Prevention (ITP) is now shipping in its staging (Canary) nightly build for minor tweaks before going into production. The latest version of Edge will include Safari’s Storage Access API which enables third-party widgets on your site to function properly.
With Safari’s most recent update to ITP, website API calls to hasStorageAccess() respond conditionally with a boolean value of “false” in third party contexts by default or “true” when there are explicit first-party user interaction permission settings to allow first party access to cookies and local storage data access in third party contexts.
Why we care. The most likely scenario for these calls is where an embedded third-party widget, like YouTube or Facebook, should be able to provide authenticated video players and comment dialogs by accessing cookies and local device storage through APIs. Without access, these embeds will not be able to function on third party websites with features that require authentication and other personalized data.
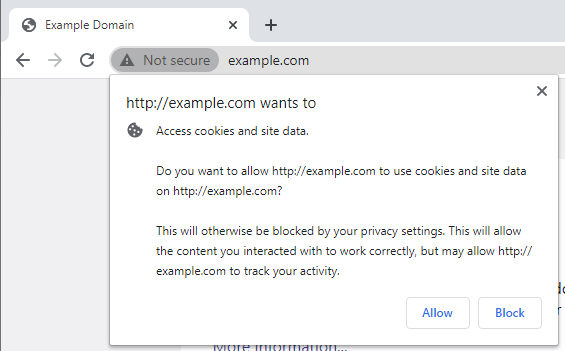
SameSite adherence. This implementation in Edge is also notable because Edge is Chromium-based which means Google’s Chrome itself (along with Edge and Firefox) adhere to SameSite rules requiring secure (TLS) https for all third-party cookies. Edge’s adoption of ITP in Chromium appears to bypass at least one SameSite restriction. With user permission as depicted below ITP will allow third party cookie access over simple http.
Third party trackers are severely limited by ITP and SameSite rules updates. All website owners need to be aware of how browsers handle the recommendations. Edge, being Chromium-based, implements SameSite but now with a significant difference. It’s uncertain whether Chrome and Chromium itself will follow suit, but Edge demonstrates how it can be done.
Pull request for Chromium. The Edge team has submitted its contribution to be taken up into the Chromium project itself. The implication of the screenshot above is that with interactive first-party user permission, Edge will bypass SameSite=None; Secure cookie restrictions and adopt Safari’s ITP data handling behavior. The condition is related by engineers as “a first party cookie in a third party context,” which when validated by user interaction should be allowed regardless of TLS connection status.
This is not yet the case for Chrome and Chromium where SameSite rules for all third party cookies require TLS in addition to a corresponding cookie value setting: SameSite=None; Secure. The Chrome team only recently announced the SameSite update to the rules, which were adopted by Edge and Firefox. Edge’s Chromium contribution now straddles both SameSite and ITP rules for third party data access.