More than a year has passed since Bloomberg Businessweek grabbed the lapels of the cybersecurity world with a bombshell claim: that Supermicro motherboards in servers used by major tech firms, including Apple and Amazon, had been stealthily implanted with a chip the size of a rice grain that allowed Chinese hackers to spy deep into those networks. Apple, Amazon, and Supermicro all vehemently denied the report. The National Security Agency dismissed it as a false alarm. The Defcon hacker conference awarded it two Pwnie Awards, for “most overhyped bug” and “most epic fail.” And no follow-up reporting has yet affirmed its central premise.
But even as the facts of that story remain unconfirmed, the security community has warned that the possibility of the supply chain attacks it describes is all too real. The NSA, after all, has been doing something like it for years, according to the leaks of whistle-blower Edward Snowden. Now researchers have gone further, showing just how easily and cheaply a tiny, tough-to-detect spy chip could be planted in a company’s hardware supply chain. And one of them has demonstrated that it doesn’t even require a state-sponsored spy agency to pull it off—just a motivated hardware hacker with the right access and as little as $200 worth of equipment.

At the CS3sthlm security conference later this month, security researcher Monta Elkins will show how he created a proof-of-concept version of that hardware hack in his basement. He intends to demonstrate just how easily spies, criminals, or saboteurs with even minimal skills, working on a shoestring budget, can plant a chip in enterprise IT equipment to offer themselves stealthy backdoor access. (Full disclosure: I’ll be speaking at the same conference, which paid for my travel and is providing copies of my forthcoming book to attendees.) With only a $150 hot-air soldering tool, a $40 microscope, and some $2 chips ordered online, Elkins was able to alter a Cisco firewall in a way that he says most IT admins likely wouldn’t notice, yet would give a remote attacker deep control.
“We think this stuff is so magical, but it’s not really that hard,” says Elkins, who works as “hacker in chief” for the industrial-control-system security firm FoxGuard. “By showing people the hardware, I wanted to make it much more real. It’s not magical. It’s not impossible. I could do this in my basement. And there are lots of people smarter than me, and they can do it for almost nothing.”
A fingernail in the firewall
Elkins used an ATtiny85 chip, about 5 millimeters square, that he found on a $2 Digispark Arduino board—not quite the size of a grain of rice, but smaller than a pinky fingernail. After writing his code to that chip, Elkins desoldered it from the Digispark board and soldered it to the motherboard of a Cisco ASA 5505 firewall. He used an inconspicuous spot that required no extra wiring and would give the chip access to the firewall’s serial port.
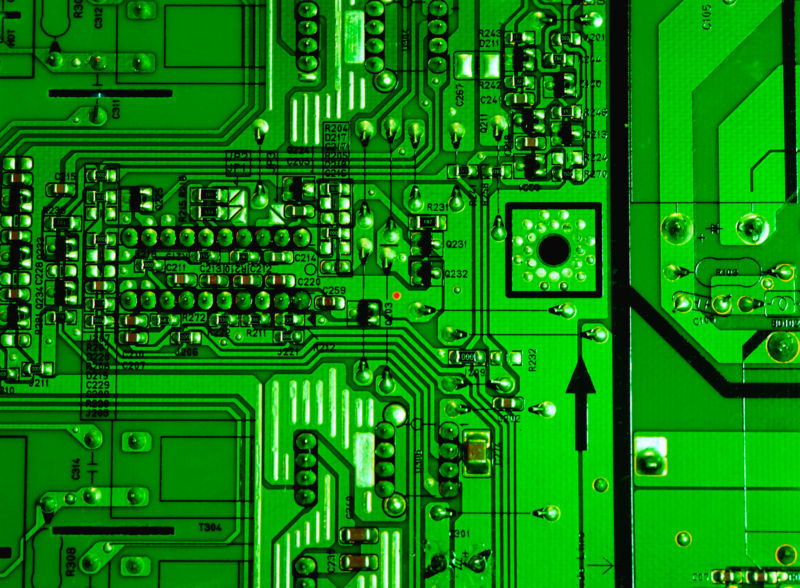
The image below gives a sense of how tough spotting the chip would be amid the complexity of a firewall’s board—even with the relatively small, 6- by 7-inch dimensions of an ASA 5505. Elkins suggests he could have used an even smaller chip but chose the ATtiny85 because it was easier to program. He says he also could have hidden his malicious chip even more subtly, inside one of several radio-frequency shielding “cans” on the board, but he wanted to be able to show the chip’s placement at the CS3sthlm conference.

Monta Elkins
Elkins programmed his tiny stowaway chip to carry out an attack as soon as the firewall boots up in a target’s data center. It impersonates a security administrator accessing the configurations of the firewall by connecting their computer directly to that port. Then the chip triggers the firewall’s password recovery feature, creating a new admin account and gaining access to the firewall’s settings. Elkins says he used Cisco’s ASA 5505 firewall in his experiment because it was the cheapest one he found on eBay, but he says that any Cisco firewall that offers that sort of recovery in the case of a lost password should work. “We are committed to transparency and are investigating the researcher’s findings,” Cisco said in a statement. “If new information is found that our customers need to be aware of, we will communicate it via our normal channels.”
Once the malicious chip has access to those settings, Elkins says, his attack can change the firewall’s settings to offer the hacker remote access to the device, disable its security features, and give the hacker access to the device’s log of all the connections it sees, none of which would alert an administrator. “I can basically change the firewall’s configuration to make it do whatever I want it to do,” Elkins says. Elkins says with a bit more reverse engineering, it would also be possible to reprogram the firmware of the firewall to make it into a more full-featured foothold for spying on the victim’s network, though he didn’t go that far in his proof of concept.
A speck of dust
Elkins’ work follows an earlier attempt to reproduce far more precisely the sort of hardware hack Bloomberg described in its supply chain hijacking scenario. As part of his research presented at the Chaos Computer Conference last December, independent security researcher Trammell Hudson built a proof of concept for a Supermicro board that attempted to mimic the techniques of the Chinese hackers described in the Bloomberg story. That meant planting a chip on the part of a Supermicro motherboard with access to its baseboard management controller, or BMC, the component that allows it to be remotely administered, offering a hacker deep control of the target server.
Hudson, who worked in the past for Sandia National Labs and now runs his own security consultancy, found a spot on the Supermicro board where he could replace a tiny resistor with his own chip to alter the data coming in and out of the BMC in real time, exactly the sort of attack that Bloomberg described. He then used a so-called field reprogrammable gate array—a reprogrammable chip sometimes used for prototyping custom chip designs—to act as that malicious interception component.
Hudson’s FPGA, at less than 2.5 millimeters square, was only slightly larger than the 1.2-millimeters-square resistor it replaced on the Supermicro board. But in true proof-of-concept style, he says he didn’t actually make any attempts to hide that chip, instead connecting it to the board with a mess of wiring and alligator clips. Hudson argues, however, that a real attacker with the resources to fabricate custom chips—a process that would likely cost tens of thousands of dollars—could have carried out a much more stealthy version of the attack, fabricating a chip that carried out the same BMC-tampering functions and fit into a much smaller footprint than the resistor. The result could even be as small as a hundredth of a square millimeter, Hudson says, vastly smaller than Bloomberg‘s grain of rice.
“For an adversary who wants to spend any money on it, this would not have been a difficult task,” Hudson says.
“There’s no need for further comment about false reports from more than a year ago,” Supermicro said in a statement.
But Elkins points out that his firewall-based attack, while far less sophisticated, doesn’t require that custom chip at all—only his $2 one. “Don’t discount this attack because you think someone needs a chip fab to do it,” Elkins says. “Basically anyone who’s an electronic hobbyist can do a version of this at home.”
Elkins and Hudson both emphasize that their work isn’t meant to validate Bloomberg‘s tale of widespread hardware supply chain attacks with tiny chips planted in devices. They don’t even argue that it’s likely to be a common attack in the wild; both researchers point out that traditional software attacks can often give hackers just as much access, albeit not necessarily with the same stealth.
But both Elkins and Hudson argue that hardware-based espionage via supply-chain hijacking is nonetheless a technical reality, and one that may be easier to accomplish than many of the world’s security administrators realize. “What I want people to recognize is that chipping implants are not imaginary. They’re relatively straightforward,” says Elkins. “If I can do this, someone with hundreds of millions in their budget has been doing this for a while.”
This story originally appeared on wired.com.