In an attempt to quell a controversy that has raised the ire of white-hat hackers, the maker of the Steam online game platform said on Thursday it made a mistake when it turned away a researcher who recently reported two separate vulnerabilities.
In its statement, Valve Corporation references HackerOne, the reporting service that helps thousands of companies receive and respond to vulnerabilities in their software or hardware. The company also writes:
We are also aware that the researcher who discovered the bugs was incorrectly turned away through our HackerOne bug bounty program, where his report was classified as out of scope. This was a mistake.
Our HackerOne program rules were intended only to exclude reports of Steam being instructed to launch previously installed malware on a user’s machine as that local user. Instead, misinterpretation of the rules also led to the exclusion of a more serious attack that also performed local privilege escalation through Steam.
We have updated our HackerOne program rules to explicitly state that these issues are in scope and should be reported. In the past two years, we have collaborated with and rewarded 263 security researchers in the community helping us identify and correct roughly 500 security issues, paying out over $675,000 in bounties. We look forward to continuing to work with the security community to improve the security of our products through the HackerOne program.
In regards to the specific researchers, we are reviewing the details of each situation to determine the appropriate actions. We aren’t going to discuss the details of each situation or the status of their accounts at this time.
Valve’s new HackerOne program rules specifically provide that “any case that allows malware or compromised software to perform a privilege escalation through Steam, without providing administrative credentials or confirming a UAC dialog, is in scope. Any unauthorized modification of the privileged Steam Client Service is also in scope.”
Kicking the hornet’s nest
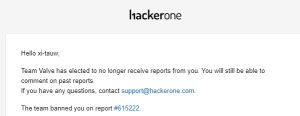
The statement and the policy change from Valve came two days after security researcher Vasily Kravets, an independent researcher from Moscow, received an email telling him that Valve’s security team would no longer receive his vulnerability reports through the HackerOne bug-reporting service. Valve turned Kravets away after he reported a Steam vulnerability that allowed hackers who already had a toe-hold on a vulnerable computer to burrow into privileged parts of an operating system. Valve initially told Kravets such vulnerabilities were out of scope and gave no indication that the one Kravets reported would be fixed.
The company later publicly denied that the issue was a vulnerability by incorrectly claiming that the exploit required hackers to have physical access to a vulnerable computer. The company went so far as to dispute the vulnerability in the advisory issued by the National Institute of Standards and Technology.
Valve’s response rankled hackers and security professionals because so-called privilege-escalation vulnerabilities are something that Google, Microsoft, and mature open source developers routinely and readily fix in their products. Valve’s contention that a demonstrated flaw of this type wasn’t a legitimate vulnerability ran counter to long-standing security norms. As criticism mounted, Valve quietly issued a patch, but researchers found that it could be bypassed. To make matters worse, Kravets on Tuesday publicly disclosed a new privilege escalation vulnerability in Steam. Valve’s Thursday statement said both vulnerabilities reported by Kravets have now been fixed.
Another researcher is shut down
Criticism grew more fevered—and began to increasingly be directed at HackerOne—after Matt Nelson, a second independent researcher, said he used the vulnerability reporting service in June to disclose one of the same Steam flaws Kravets found. According to an exchange Nelson posted, a HackerOne representative said the vulnerability was out of scope to qualify for Valve’s bug bounty program. When Nelson replied that he wasn’t looking for money but instead only wanted the public to be aware of the vulnerability, the HackerOne representative asked Nelson to “please familiarize yourself with our disclosure guidelines and ensure that you’re not putting the company or yourself at risk. https://www.hackerone.com/disclosure-guidelines.”
Those guidelines specifically state, “Please note that we will not consent to disclose reports if they have been marked out-of-scope or inapplicable, or where Valve has not taken a specific corrective action / mitigation.”
The HackerOne representative also locked the thread so that it no longer could be read. Nelson told Ars he was surprised by HackerOne’s response. Using the abbreviation for non-disclosure agreement, he wrote in an email:
I wouldn’t go as far as calling it an NDA, but they certainly were implying there could be repercussions for violating Valve’s policy or HackerOne’s disclosure policy. My reaction is that I could care less. If they want to ban a researcher submitting bugs in good faith, they certainly can. I’m not reporting via HackerOne to make money, it simply seemed like the easiest way to get in contact with them. Making the process more difficult for those willing to report vulnerabilities does absolutely nothing but hurt them and the general public.
Nelson then reported the vulnerability directly to Valve. Valve, he said, acknowledged the report and “noted that I shouldn’t expect any further communication.” He never heard anything more from the company.
Shifting the blame
Nelson said he welcomed Valve’s admission that it was a mistake for Valve to have turned away Kravets and the policy change that makes privilege-escalation vulnerabilities in scope.
“I can certainly believe that the scoping was misinterpreted by HackerOne staff during the triage efforts,” Nelson wrote. “It is mind-blowing to me that the people at HackerOne who are responsible for triaging vulnerability reports for a company as large as Valve didn’t see the importance of Local Privilege Escalation and simply wrote the entire report off due to misreading the scope.”
At the same time, he added, Valve should take more responsibility for the role it played in the bungled response.
“Valve can shift the blame to HackerOne as much as they would like, but the fact that they took the time to actually dispute the CVE Mitre issued means that they don’t see the issue as a legitimate vulnerability, regardless of how HackerOne handled triaging it.”
In a post reporting the first vulnerability, Kravets also said that HackerOne staff told him he wasn’t permitted to publicly disclose the vulnerability.
Meanwhile, he also told Ars on Thursday morning that he had yet to receive any communication from Valve and that he remained locked out of the Valve bug-reporting section of HackerOne.
Vasily Kravets
A HackerOne spokeswoman told Ars:
We aim to explicitly communicate our policies and values in all cases and here we could have done better. Vulnerability disclosure is an inherently murky process and we are, and have always been, committed to protecting the interests of hackers.
Our disclosure guidelines emphasize mutual respect and empathy, encouraging all to act in good faith and for the benefit of the common good.
Still cause for concern
While Valve’s admission and policy change are encouraging, HackerOne’s barring of Kravets remains an ongoing concern. HackerOne helps thousands of organizations receive and respond to vulnerability reports. Its policies have a huge effect on the security of products and devices used all over the world, said Katie Moussouris, founder and CEO of Luta Security who wrote the disclosure policies here and here, adopted by the International Organization for Standardization, while at Microsoft.
“Silencing the researcher on one issue is in complete violation of the ISO standard practices, and banning them from reporting further issues is simply irresponsible to affected users who would otherwise have benefited from these researchers continuing to engage and report issues privately to get them fixed,” Moussouris told Ars. “The norms of vulnerability disclosure are being warped by platforms that put profits before people.”